UDP File Transfer vs. Traditional Protocols: A Deep Dive into Performance
May 29, 2024In the ever-evolving landscape of digital communication, UDP (User Datagram Protocol) file transfer stands out as a beacon of speed and efficiency.

In this comprehensive guide, we'll unravel the secrets behind UDP file transfer in 2025, delving into its definition, applications, and recommended solutions for optimized performance.
Quick View of UDP File Transfer
UDP stands for User Datagram Protocol. It's one of the core communication protocols of the Internet Protocol (IP) suite, operating at the Transport Layer (like its counterpart, TCP).
It's connectionless. Unlike TCP, UDP doesn't establish a dedicated connection (no "handshake") before sending data. It just sends packets (called datagrams) to the destination.
"Fire and Forget": Because it doesn't set up a connection or manage packet delivery, it's often described as a "fire and forget" protocol.
Speed over Reliability: UDP prioritizes speed and low overhead (smaller headers, less processing) over reliability.
No Guarantees: It provides no guarantees that:
- Datagrams will arrive.
- Datagrams will arrive in the correct order.
- Datagrams won't be duplicated.
- It doesn't manage network congestion.
Use Cases: Ideal for applications where speed is more critical than perfect reliability, and where handling lost packets (if necessary) can be done by the application itself. Common examples include:
- Streaming video and audio (minor glitches are often acceptable)
- Online gaming (real-time updates are crucial)
- Voice over IP (VoIP)
- DNS (Domain Name System) queries
- TFTP (Trivial File Transfer Protocol)
In essence, UDP is a fast, lightweight way to send data when you don't need the guaranteed delivery and overhead of TCP.
4 Differences Between UDP File Transfer and Other Protocols
UDP file transfer differs from other file transfer methods in a key aspect: prioritization of speed over guaranteed delivery. Here's a breakdown of the key differences:
Reliability:
- UDP: Less reliable. Packets can be lost or arrive out of order with no mechanism to ensure they arrive or are retransmitted. This is suitable for real-time applications where a slight glitch is acceptable but not for critical file transfers.
- Other protocols (e.g., TCP): More reliable. They establish a connection, check for errors, and resend lost packets, ensuring complete and accurate data delivery. This is ideal for standard file transfers where data integrity is crucial.
Speed:
- UDP: Faster. By skipping connection setup and error checking, UDP prioritizes speed. This is beneficial for large file transfers on high-bandwidth networks where speed is the main concern.
- Other protocols (e.g., TCP): Slower. The extra steps for reliability add some overhead, making transfers slightly slower.
Connection:
- UDP: Connectionless. It simply sends data packets without establishing a dedicated connection, similar to sending postcards.
- Other protocols (e.g., TCP): Connection-oriented. They set up a dedicated connection like a phone call, ensuring a reliable pathway for data transfer.
Use Cases:
- UDP: Ideal for real-time applications like video streaming, online gaming, and VoIP calls where a slight delay is tolerable but occasional data loss is acceptable. It can also be useful for large file transfers on high-bandwidth networks where speed is a priority.
- Other protocols (e.g., TCP): Used for most file transfers (FTP, SFTP, etc.) where data integrity is crucial and occasional slowdowns are acceptable for a complete and accurate transfer
Here's an analogy:
Imagine sending a document across town.
- UDP: You write the document, address it, and throw it in the mail. It might arrive quickly, but there's a chance it gets lost or arrives with some pages missing.
- Other protocols (e.g., TCP): You use a registered mail service that ensures the document reaches its destination complete and undamaged, but it might take a bit longer.
3 Recommended Tools for UDP File Transfer
In the dynamic realm of technology, advancements and innovations continuously redefine the landscape of UDP file transfer solutions.
While the top three solutions outlined provide exemplary performance and reliability, it's crucial for organizations to stay attuned to emerging trends and developments.
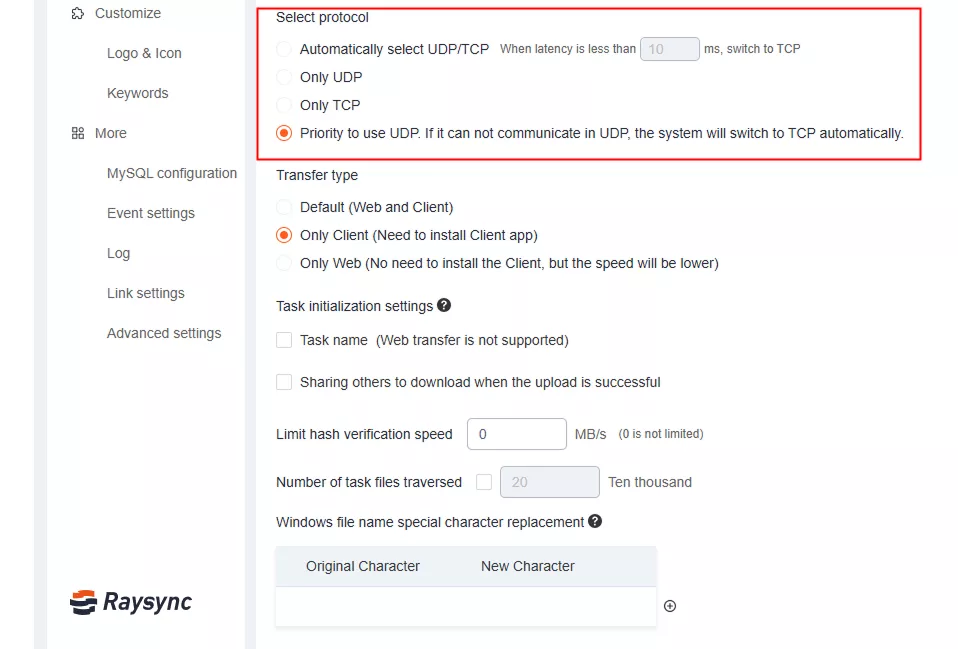
1. File Transfer over UDP - Raysync
Raysync is designed for rapid file transfer over UDP, which excels in facilitating large-scale data transmission.
Leveraging intelligent routing, protocol optimization, and encryption, Raysync also ensures rapid and secure file transfer over UDP, catering to diverse enterprise needs.
Its user-friendly interface and comprehensive support make it an attractive choice for businesses seeking reliable and efficient file transfer capabilities.
2. Resilio
Resilio offers a peer-to-peer file synchronization and transfer solution powered by UDP for efficient data exchange.
With its resilient architecture and decentralized approach, Resilio is well-suited for distributed environments and bandwidth-intensive applications, ensuring seamless file transfer experiences.
Its adaptive bandwidth management and robust data integrity checks make it a preferred choice for organizations needing efficient and scalable file transfer solutions.
3. Aspera
Aspera's UDP-based file transfer solutions are tailored for high-speed data movement, particularly in media and entertainment, healthcare, and research sectors.
Employing patented FASP® (Fast, Adaptive, Secure Protocol) technology, Aspera achieves exceptional transfer speeds over long distances and challenging network conditions, ensuring optimal performance.
Its ability to handle large files and maintain high transfer rates even under suboptimal network conditions makes it indispensable for industries requiring reliable and fast data transfer.
FAQs about UDP File Transfer
If you have any questions related to UDP file transfer, here is something you definitely look at.
1. Can UDP Be Used for File Transfer
Yes, UDP is suitable for file transfer, especially in scenarios prioritizing speed over reliability. It is particularly useful for applications where minor data loss is acceptable, and speed is crucial.
2. What Is the Difference Between TCP and UDP File Transfer
TCP offers reliable, connection-oriented communication with error checking and retransmission mechanisms, whereas UDP prioritizes speed over reliability without guaranteed delivery or error correction.
This makes TCP suitable for applications requiring data integrity, while UDP is ideal for real-time applications where speed is more critical.
3. What Is a UDP File
A UDP file refers to a file transfer using the UDP protocol, operating at the transport layer of the OSI model, providing a connectionless communication service. This type of file transfer emphasizes rapid delivery and is used in scenarios where quick transmission is more important than absolute reliability.
Who Benefits Most from UDP File Transfer
Several industries can benefit from UDP file transfer, especially when prioritizing speed over guaranteed delivery. Here are some prominent examples:
- Media and Entertainment
- Healthcare
- Scientific Research
- Finance
- Content Delivery Networks (CDNs)
General points to consider for UDP file transfer suitability:
- Network quality: UDP performs best on high-bandwidth, reliable networks where data loss is unlikely.
- Data criticality: If data corruption is unacceptable, UDP might not be suitable.
- Error handling mechanisms: When using UDP, it's important to have mechanisms in place to detect and potentially recover from data loss.
It's important to remember that UDP is just one tool in the toolbox. The most suitable file transfer method depends on the specific needs and priorities of the situation.
Conclusion
As we traverse through 2025, UDP file transfer remains a cornerstone in industries requiring swift data transmission. Despite its trade-offs in reliability, UDP-based solutions power critical applications like media streaming, content delivery, and distributed computing, driving efficiency in the digital realm. By grasping the nuances of UDP file transfer and adopting recommended solutions, organizations can navigate the digital landscape with unparalleled speed and agility.
You might also like

Industry news
May 29, 2024Dive into the world of UDP file transfer in 2025, uncovering its intricacies, speed, and applicability. Explore the protocol, its comparisons with TCP, and discover top-notch solutions for seamless file transfer over UDP.
![Best 3 Tools for Secure P2P File Transfer [Priority to Security]](http://images.ctfassets.net/iz0mtfla8bmk/7l67cXNVgTWMLijr8H6AyG/9e324bd15df4a3f769accb487738fcf2/secure-p2p-file-transfer.png)
Industry news
September 27, 2024Prioritizing security and encryption, discover the best tools for secure p2p file transfer and learn how to ensure data protection.

Industry news
November 27, 2024Delve into the world of AWS File Transfer in 2025. Explore its features, pricing, and ideal use cases. Discover if it's the right solution for your file transfer needs.